
What are social engineering attacks-Examples and Tips to prevent
Social Engineering is the art of manipulating people to give up confidential information using a variety of techniques and methods. Many don’t realize that just a few pieces of information can give criminals access to multiple networks and accounts. Social engineers use both online and offline means to lure users into compromising their security, transferring money, or giving away sensitive information. They try to take advantage of basic human nature to trick individuals into this purpose.
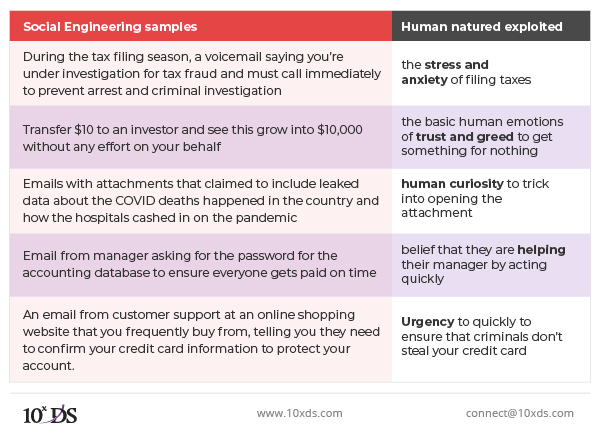
Why do they target people? Because people are considered to be the weakest link in the security chain. Social engineering can be challenging to contain into a single formula because criminals leverage existing socio-political scenarios and multiple compliance-related scenarios to trick a person. It’s one of the reasons most data breaches involve the human element. Emotional manipulation gives attackers the upper hand in any interaction. The below tables list out a few samples and basic human nature that criminals try to exploit. It is hard to find out whether it is a legitimate request or not while a person is stressed or in an urgency.
Types of Social Engineering attacks
Phishing is the most common type of social engineering attack. Attackers pretend to be a trusted institution or individual in an attempt to persuade you to expose personal data and other valuables. Phishing generally exploits people by infected email attachments or links to malicious websites. Spam phishing is a widespread attack aimed at many users while spear phishing uses personalized information to a specific target user. The other types are:
- Angler phishing – Attacks using bogus corporate social media accounts.
- Pharming – redirect a website’s traffic to a malicious site that impersonates it
- Tabnabbing– Manipulates open inactive web pages and redirects to a duplicate one that they control.
- BEC (business email compromise) – Highly targeted phishing attack in which fraudsters trick people into handing over money or corporate data
- Whaling – exploits the influence senior executives have over lower-level roles, such as CEOs over financial executives or assistants.
Baiting, Diversion theft, Honey trap, Smishing, Vishing, Pretexting, Quid pro quo, Scareware, Water-holing and Tailgating etc are few other types of social engineering and this is still evolving as cybercriminals find newer ways to trick people. Social media, email, text messages are common targets, but you’ll also want to account for in-person interactions as well.
1. Build a method to report any suspicious things and contain the attacks.
2. Train the staff to be cautious about for not falling victim to social engineering and test the effectiveness of the training often.
- If your emotional state is elevated (fear, curiosity, excitement, etc) pause and evaluate the consequences of your action.
- Check email addresses and social media profiles when getting a message with links or attachment
- Check if the website is legitimate by noticing irregularities in the URL, poor image quality, old or incorrect company logos, and webpage typos
- If a link or file name appears vague or odd in a message, check it twice as:
- a link as it may be infected with malware so the criminal can take over the machine and collect your contacts information or any other client information
- download of pictures, music, movie, document, etc., that has malicious software embedded which can give the criminal access to machine, email account, social network accounts and contacts, and the attack spreads to everyone you know
3. Organizations should implement technological cyber security measures – including firewalls, antivirus and anti-malware, patch management and penetration testing, and access management policies. This will help limit the number of attacks reaching your staff and minimise the damage from any successful attacks Implement technological security measures.
Conclusion
By appealing to human emotions like curiosity and terror, social engineers are able to carry out their designs and lure their victims into their traps. Always proceed with caution anytime an email, a website’s offer or a random piece of digital media makes you feel uneasy. Most attempts at social engineering in the online world can be avoided by simply keeping your guard up.
Talk to our experts to know more about how to safeguard your organization from social engineering attacks.


